Notice: This Wiki is now read only and edits are no longer possible. Please see: https://gitlab.eclipse.org/eclipsefdn/helpdesk/-/wikis/Wiki-shutdown-plan for the plan.
Difference between revisions of "PDS Architecture"
(→Personal Data Store) |
(→Personal Data Store) |
||
| Line 19: | Line 19: | ||
===Personal Data Store === | ===Personal Data Store === | ||
| − | A [[Personal Data Store 2.0]] is a | + | A [[Personal Data Store 2.0]] is a web service that stores personal (self-asserted) data, that makes it available to apps on a user-permissioned basis. |
| − | + | ||
| − | + | ||
===PDS Client === | ===PDS Client === | ||
Revision as of 11:40, 30 March 2010
{{#eclipseproject:technology.higgins|eclipse_custom_style.css}}
Higgins 1.0 and 1.1 services
Web Services
- I-Card Manager
- Thin client selectors use the I-Card Manager Google GWT-based app to provide a web interface to view, update and manage your cards hosted on the I-Card Service.
- I-Card Service
- Some selectors are designed as "thin clients" that only implement the user interface portion and rely on a hosted I-Card Service 1.1 for core functionality.
- CardSync Service 1.1
- A specialized bi-directional, synchronizing XML endpoint for synchronizing i-card data stored on a co-resident I-Card Service 1.1
Web Apps
- Cloud Selector 1.1
- Makes i-cards available as OpenIDs. It reads card data from the I-Card Service, so no client software is required.
Higgins 2.0 PDS
Under development for Higgins 2.0
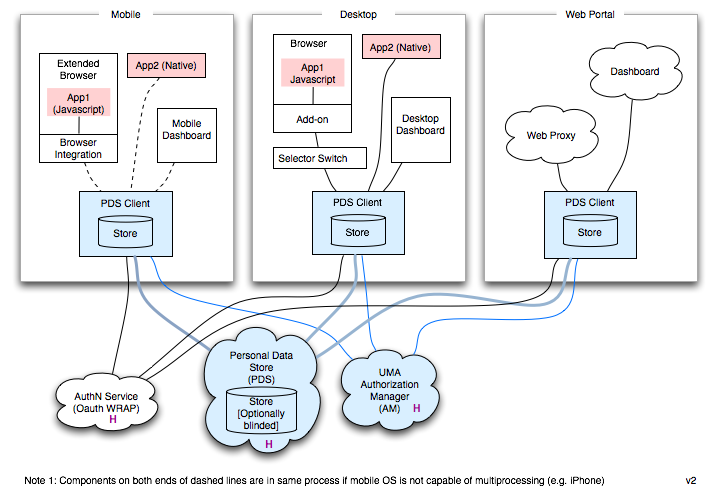
Personal Data Store
A Personal Data Store 2.0 is a web service that stores personal (self-asserted) data, that makes it available to apps on a user-permissioned basis.
PDS Client
The PDS Client has no UI, but performs a number of functions:
- The “main event” is support for apps that wish to read attributes from the PDS by calling methods like “getAttribute()”. The PDS client also maintains (also in the PDS) the user’s permissions–the decisions that the user has make as to who (what app or relying party) has access to what attributes. The first time a new app/RP asks for a certain set of attributes, the PDS Client will trigger the PDS Dashboard to present the policy decision to the user. The next time this same request happens, the PDS Client remembers the grant and usually doesn’t have to bother the user about it this time.
- The PDS client maintains a local copy of some or all of the person’s personal data stored in the remote PDS
- It maintains an OAuth WRAP access token that it gets by authenticating itself to an external authentication service. It passes this token along in XDI messages to the remote PDS service.
- It can be configured to encrypt attribute values before they are sent over the wire (e.g. in XDI messages) to the remote PDS
- It contains a local Security Token Service (STS) that allows it to create and sign SAML (for example) tokens for self-asserted attributes.
- It contains an STS client to support remote IdP/STSes managed by external parties (e.g. to support managed i-cards).
- It performs cross context schema mapping. The PDS Client is packaged as either a C++ or Java code library or as a separate operating system process (e.g. on Windows it is a Windows Service).
Authentication (AuthN) Service
The IdAS Proxy Service 1.1 and Attribute Service 1.1 require access tokens minted by the Authentication Service 2.0. Eventually the I-Card Service and CardSync Service will also rely on this external authN service.
Authorization Manager
- Authorization Manager (planned) gives the user control over the flows of data from a managed relationship card provider to a relying party. We plan to use/adapt Kantara UMA protocols.
Web Portal
- We plan to develop a Web Portal--an evolution of the Cloud Selector 1.1 from Higgins 1.1 with broader functionality.
Misc. Building Blocks
This section describes the data related services, java frameworks and data models that are used by the personal data agent services.
Data Models
- Data Models used in Higgins code and services
IdAS Solution
The IdAS solution is a testbed for exercising the IdAS Java framework.
- Higgins 1.1: See Higgins_1.1_Plan#IdAS_Solution_1.1
- Higgins 1.0: IdAS Solution 1.0: a basic configuration of the Identity Attribute Service 1.0 (IdAS). IdAS is a java framework that provides a common interface to identity, profile, and relationship data from external data sources (e.g. websites, databases, directories).
XDI4J
XDI4J is a java library for working with XDI.
- Higgins 1.1: XDI4j 1.1